If you need help with downloading and installing Kali Linux on your virtual machine, the following tutorials will help.
https://www.untaggedmoron.com/2022/05/download-right-kali-linux-for-your.html
https://www.untaggedmoron.com/2022/05/install-kali-linux-on-vmware-virtual.html
In this tutorial, I might me mentioning about tor service. But by this, I’m not asking you to use tor browser and hide your IP. Instead, we will be using tor service to hide our IP, while using browsers such as firefox and scanning programs such as nmap.
Enter your Terminal -> Ctrl + Alt + T
You need to download proxychains
sudo apt-get install proxychains
In Kali, by default the proxychains will be installed. But there is no harm in running the code, to make sure.
Now you need to download tor service. (Plz note, you are not downloading tor browser).
sudo apt-get install tor
Now you need to enable tor service,
sudo systemctl enable tor.service
If you see and option to hover your mouse to hilight tor.service, do that and click enter. In my experience, I never had that option. If not, ignore it.
Now start the tor service
sudo systemctl start tor.service
And you can check the status of your tor service
sudo systemctl status tor.service
Now hit ‘Q’ alphabet key in keyboard to enter typing mode.
Run the following command to edit your installed proxychain app. You might need to tweak it a bit to make it work as intended.
sudo vim /etc/proxychains.conf
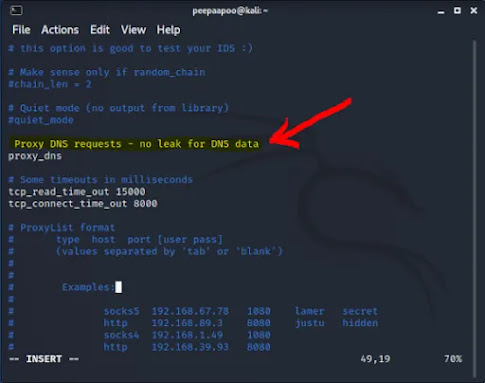
You will see a screen, as shown below.
In the pic above, I have marked 1 & 2.
You need to delete # in front of dynamic_chain.
Also you need to add # in front on strict_chain.
In order to edit, you might need to,
hit i – the aplphabet key and use arrow keys to scroll.
Please do not mess up the screen, before pressing i.
To exit the editing mode, hit ESC key.
If you want to know why we need to do this, read the description given under each chain.
If you choose random_chain, it will only substitute your ip with one random proxy server, which is least secure.
If you choose strict_chain, it will alter your ip through multiple (x4) proxy servers, very strictly. But it always have an order, so easy to track. Also if one of these proxy server is down, you wont be acheiving a connection.
The benefit of dynamic_chain is, it will use multiple proxies to alter your ip in different order. Also if one of the proxy server is down, it will automatically skips to the next. Ain’t that cool.
Now scroll down your screen to reach the part mentioned in the area.
You may delete the # in front of Proxy DNS requests – no leak for DNS data.
Anyway this is optional. Doing this will hide your identity better than the otherwise.
The reason is, even if you mask your ip with how many number of proxies, you can be tracked with your DNS.
If you will do it, the screen should look like,
(please dont forget to hit i – alphabet key to edit and then press ECS key after you are done)
I dont mind doing this, as I have no intentions to hack anyone 😉
I use IP spoofing to access some websites, which are blocked by default by my internet provider, which is not a criminal offense.
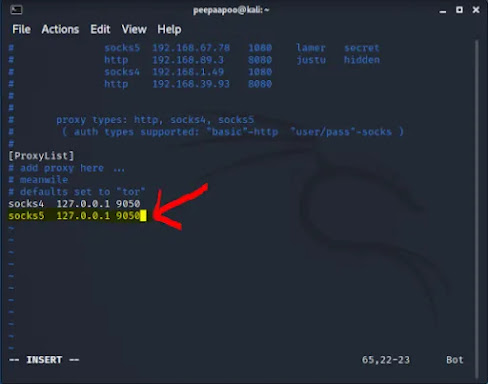
Now scroll to reach almost last of the screen to find,
Below that line add the following line,
socks5 127.0.0.1 9050
Better you type this line mannually (hit i alphabet key for doing that).
After typing socks5, hit TAB key to align with perfect spacing and then type the rest.
It should look like this
Now hit ESC key. And type the below code strictly.
:wq
Hit ENTER key.
Your proxychains are about to deploy now.
Lets see how it works.
Close your Firefox browser, if its open by any chance.
Type the following in terminal,
proxychains firefox duckduckgo.com
This will open your firefox, with the search engine site duckduckgo.com open.
Now enter any IP checking site such as: http://www.dnsleaktest.com
Hit standard test and you will see your IP and country changed.
You may use google.com or any other site instead of duckduckgo.com.
This firefox session will continue to connect through tor proxychains service, untill you close the firefox.
So browse any website, during the session.
Also closing the process going on in terminal will terminate the firefox session.
Note: As you are getting connected through tor.service, the speed of browsing may be slower than the normal. Because your connection is being channelled or tunnelled through different proxy servers worldwide.
Additionally, some websites may block tor connection nodes for security reasons.
To use NMAP with proxychains
proxychains nmap [TYPE THE VARIABLE]
For eg: proxychains nmap -sV -sT
You may replace tor proxy with any other proxy and port, available…
Disclaimer : for educational purpose only… 😉